
Stakeholder Data Security: Best Practices for Accountants

Jan 8, 2026
Practical UK-GDPR aligned security steps for accounting firms: role-based access, encryption, MFA, staff training, incident plans and vendor audits.
Protecting sensitive data is a non-negotiable responsibility for accounting firms. Mishandling client information can lead to financial fraud, hefty fines under UK GDPR, and a damaged reputation. With stricter rules introduced by the Data (Use and Access) Act 2025, firms must prioritise robust security measures to stay compliant and maintain trust.
Key takeaways:
Top threats: Phishing attacks, ransomware, and poor cloud configurations expose sensitive data.
Compliance focus: UK GDPR Article 32 requires technical and organisational safeguards, such as encryption and access controls.
Action steps: Implement role-based access, train staff on security awareness, and use secure platforms like neoeco for data management.
Incident readiness: Have a clear response plan for breaches, including the 3-2-1 backup rule and vendor security assessments.
Strong security practices - like encryption, multi-factor authentication, and regular audits - are critical to protecting data and meeting compliance standards. Neglecting these measures could lead to severe financial and reputational consequences.
Auditing and Controlling Cybersecurity Risks
Data Security Challenges Facing Accounting Firms
Accounting firms are increasingly grappling with a variety of security threats, each with the potential to cause significant damage. These challenges take on several forms, as outlined below.
Phishing Attacks and Cyber Threats
Phishing continues to be the most prevalent method used by attackers. Cybercriminals often impersonate suppliers, regulators, or even high-ranking employees to deceive staff into sharing passwords or sensitive technical details. Once they gain access, these attackers frequently deploy ransomware to encrypt critical data, demanding payment - usually in cryptocurrency - for its release.
High-profile incidents, such as those affecting the NHS, Royal Mail, and Travelex, demonstrate how devastating such attacks can be, disrupting essential operations. For firms handling both financial and sustainability data, the fallout from a breach can be particularly severe.
In addition to external threats, poor data-sharing practices within organisations can further expose valuable information to risk.
Data Exposure in Shared Reports and Cloud Systems
Collaboration tools like SharePoint and Google Drive have become indispensable, but they also come with vulnerabilities. A common issue is improperly configured permissions, which can leave files accessible to unauthorised users. Hackers often exploit this by using specialised tools to locate and extract sensitive data.
The danger escalates when employees turn to unauthorised file-sharing services to move large sustainability datasets outside the firm's secure systems. Even when using approved cloud platforms, there are risks tied to where the data is stored. Hosting data in regions with differing legal frameworks can lead to breaches of UK GDPR regulations, particularly when jurisdictional protections fall short.
As firms navigate these exposure risks, they must also contend with increasingly stringent regulatory requirements.
UK GDPR and Regulatory Compliance Risks
Under Article 32 of the UK GDPR, firms are obligated to adopt security measures that match the level of risk, factoring in the latest technological advancements and the specific nature of the data they handle. This includes implementing both technical and organisational safeguards. Firms must evaluate the potential consequences of breaches involving sensitive stakeholder information - whether financial records, carbon footprint data, or supplier details - and adjust their security protocols accordingly.
Systems must ensure the confidentiality, integrity, and availability of data. When relying on third-party platforms for tasks like carbon accounting or aligning ESG data with ISSB standards, firms need to confirm these providers meet the security standards set by Article 32.
Understanding these complex challenges is a critical step toward developing effective data protection strategies.
How to Protect Stakeholder Data
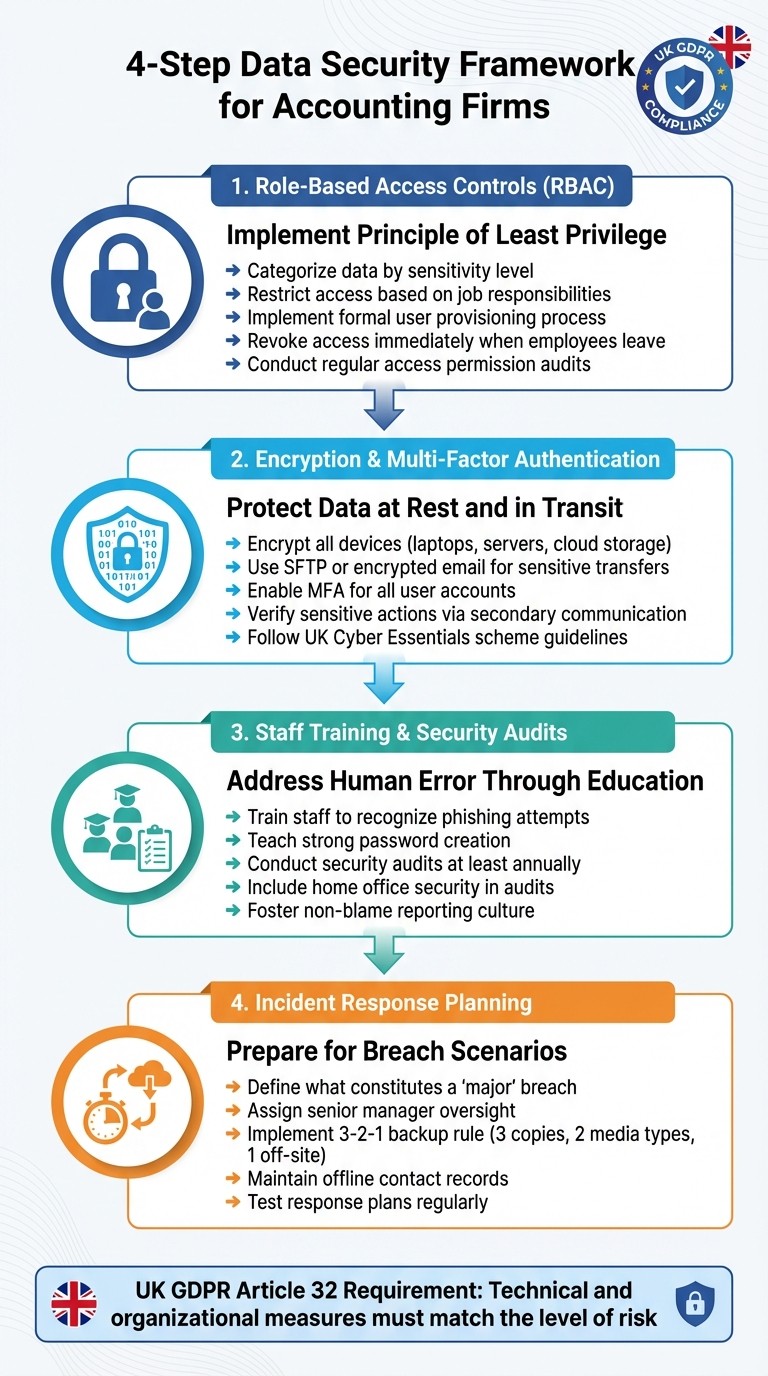
4-Step Data Security Framework for Accounting Firms Under UK GDPR
Once organisations grasp the threats they face, the next step is putting effective safeguards into action. The following measures address frequent vulnerabilities while helping organisations meet their obligations under UK GDPR Article 32. These steps not only protect data but also ensure compliance with GDPR requirements.
Set Up Role-Based Access Controls
Role-based access control (RBAC) limits access to sensitive information based on job responsibilities. It follows the "principle of least privilege" - employees should only access the data necessary for their tasks.
Start by categorising data according to its sensitivity. For instance, general financial records might be accessible to most of the team, but highly sensitive data, like client bank details, should be restricted to a small, authorised group. Work with your IT team to implement a formal user access provisioning process that covers all staff, including temporary workers and third-party contractors.
"Role-based access ensures that only those who need specific data to perform their job functions can access it, reducing the risk of unauthorised access or data breaches." - The Educational Foundation for Women in Accounting
Don’t overlook the "leaver process" - revoke access immediately when employees change roles or leave the organisation. Regularly review access permissions by auditing user logs to ensure they still align with current responsibilities. For firms handling sensitive sustainability data, such as carbon accounting or ISSB reporting, this is especially critical when managing both financial and environmental datasets.
To strengthen this further, encryption measures will add another layer of security.
Apply Encryption and Multi-Factor Authentication
After setting up access controls, data protection can be enhanced with encryption and multi-factor authentication (MFA).
Encryption safeguards data both when it’s stored and during transfer. UK GDPR Article 32 specifically highlights encryption as an effective technical measure.
Ensure all devices - laptops, servers, and cloud storage - are encrypted, with additional layers for high-risk data like payment information. When sharing sensitive reports or datasets externally, use Secure File Transfer Protocol (SFTP) or encrypted email services instead of unprotected channels.
MFA adds a second layer of security, making it harder for unauthorised users to gain access. For particularly sensitive actions, such as updating client bank details, verify instructions through a secondary communication method, like a phone call to a verified contact, to prevent phishing scams.
"Encrypting data when it is stored (at rest) and when it is in transit can mitigate the worst effects of hackers." - RICS
The UK government's Cyber Essentials scheme offers a solid starting point for implementing encryption and access management controls.
Train Staff and Run Security Audits
Human error is a leading cause of data breaches, whether it’s forgetting to use the BCC field in emails or falling for phishing scams. Regular training can help staff recognise phishing attempts, create strong passwords, and report any data-handling issues to a security officer.
Conducting security audits is another key step. These audits help identify and address vulnerabilities in your network. Review and document risks to all data held by the organisation at least once a year.
Don’t forget to include home office security practices in your audits. Encourage an open, non-blame culture to ensure staff feel comfortable reporting breaches promptly.
Software and Technology for Secure Data Management
Modern software has reshaped data management by combining security, compliance, and automation - essential elements for effective sustainability reporting and adherence to UK GDPR regulations. These tools ensure that robust security measures, like encryption and role-based access, function smoothly and efficiently.
Secure Platforms for Carbon and Sustainability Reporting
When choosing sustainability reporting software, prioritise platforms that comply with standards such as SOC 2 and GDPR. These certifications indicate that the software employs enterprise-grade encryption, access controls, and auditing capabilities to safeguard stakeholder data.
Take neoeco, for example. This platform is tailored for accounting firms and integrates seamlessly with popular systems like Xero, Sage, and QuickBooks to extract transaction data directly. It offers advanced client-level access controls, allowing firms to provide specific permissions to auditors or reviewers without risking sensitive information exposure.
neoeco operates on the principles of Financially-integrated Sustainability Management (FiSM), automatically mapping transactions to established emissions categories under frameworks such as GHGP, ISO 14064, SECR, and UK SRS. Its centralised Policy and Evidence Hub securely stores invoices and supporting documents, simplifying audits and reducing the risks associated with scattered communications. For firms handling Scope 3 emissions across multiple clients, neoeco’s white-labelling feature enables them to produce branded, audit-ready reports while maintaining strict data security.
Reducing Manual Errors with Automation
In addition to secure access, automation plays a crucial role in safeguarding data integrity by cutting down on human error. Spreadsheets often compromise security and accuracy due to broken formulas, outdated data, and manual inputs. Automated platforms like neoeco address these issues by using activity-based transaction matching to align financial records with the appropriate emissions categories. This not only reduces calculation times to as little as two days but also significantly decreases the likelihood of manual mistakes.
Incident Response Plans and Compliance Policies
Even the most secure systems can fall victim to breaches. What sets a contained incident apart from a full-blown crisis is preparation. A well-structured incident response plan allows your firm to act swiftly, reduce damage, and stay compliant with regulatory requirements under UK GDPR.
Build a Cybersecurity Incident Response Plan
Start by clearly defining what constitutes a 'major' breach - such as those affecting critical operations, financial systems, or sensitive stakeholder data. Without clear definitions, response efforts can become unnecessarily delayed.
Assign a senior manager to oversee security risks and ensure roles are well-defined for emergency actions, like notifying IT support teams and regulators. Detection mechanisms, such as firewalls and anti-virus software, should be in place to flag unusual activity early, rather than waiting for systems to fail. Keep an up-to-date list of key contacts, including IT specialists, regulators, suppliers, and essential clients.
Business continuity planning is just as important. Identify which operations can continue using alternative methods, like offline tools or manual processes, while primary systems are being repaired. Always maintain an offline, secure record of client contact details so communication remains possible in the event of a network compromise. Follow the 3-2-1 backup rule: keep three copies of your data on two different media types, with at least one stored off-site. This approach can be a lifesaver when dealing with ransomware.
"The measures must also enable you to restore access and availability to personal data in a timely manner in the event of a physical or technical incident." - Information Commissioner's Office (ICO)
Real-world examples highlight the importance of these plans. In January 2023, Royal Mail faced a ransomware attack that disrupted international mail operations, showcasing the need for recovery strategies for critical functions. Similarly, in 2022, NHS services in England were significantly impacted when "LockBit" malware disabled digital records, forcing hospitals to revert to manual processes for weeks. Perhaps the most striking example is Travelex, which suffered a devastating ransomware attack in 2019, contributing to its eventual administration just months later.
Once your internal response plan is solid, the next step is ensuring your vendors meet stringent security standards.
Assess Vendor Security and Compliance
While securing your internal systems is essential, the security of external vendors is equally critical to protecting sensitive data. Outsourcing doesn’t exempt you from legal responsibilities - accountants must ensure customer data remains secure and that suppliers meet compliance requirements. Under Article 32 of UK GDPR, contracts must mandate that processors implement technical and organisational measures comparable to those of the controller.
Before partnering with any vendor, confirm they hold certifications like SOC 2 or ISO 27001, which indicate adherence to enterprise-grade security standards. Check whether they use encryption for data both at rest (stored on servers) and in transit (during transfer). Be aware of where their cloud servers are physically located, as the jurisdiction's regulations will determine data protection obligations. Contracts should also include clauses granting the right to audit and inspect data processors to ensure compliance with security standards.
Platforms such as neoeco exemplify strong vendor security practices. By integrating seamlessly with systems like Xero, Sage, and QuickBooks, neoeco eliminates the need to transfer sensitive financial data through insecure methods like USB drives or email attachments. Its adherence to SOC 2 standards and use of Stripe for payment processing - a provider with top-tier certifications in the payments industry - ensures client data remains secure throughout the reporting process.
Finally, test your incident response plan regularly with tools like vulnerability scans, penetration tests, and phishing simulations. Document all actual and potential security incidents to support regulatory reporting and prepare for future audits. Use standardised reporting forms to ensure that staff and partners can quickly and accurately record all necessary details when incidents occur.
Conclusion
Protecting data isn’t just a legal requirement under UK GDPR - it’s also the bedrock of client trust. Article 5(f) of the UK GDPR, often referred to as the "security principle", makes it clear: personal data must be safeguarded with technical and organisational measures to prevent unauthorised access, loss, or damage. Without strong security practices, client trust can quickly erode.
A solid defence strategy involves a mix of strong internal controls - like role-based access, encryption, and multi-factor authentication - paired with secure, automated platforms. For example, tools such as neoeco integrate seamlessly with accounting systems like Xero, Sage, and QuickBooks, helping minimise data exposure while maintaining full SOC 2 and GDPR compliance. These tools allow firms to produce audit-ready sustainability reports without putting sensitive stakeholder data at risk. However, technology alone isn’t enough; continuous testing and monitoring are equally vital to ensure these measures remain effective.
Compliance is not a one-off task. UK GDPR mandates regular testing and evaluation of security measures to ensure they adapt to emerging risks. Ongoing assessments demonstrate accountability, reassuring both regulators and clients that your firm takes data protection seriously.
FAQs
How can accounting firms protect themselves from phishing attacks?
Phishing attacks, where fraudulent emails or messages are used to trick individuals into sharing sensitive information, pose a serious threat to accounting firms that deal with confidential client data. To combat this, it’s crucial to train your team regularly. Teach them to recognise suspicious emails, verify the authenticity of senders, hover over links before clicking, and report any unusual activity immediately. On top of this, enforce multi-factor authentication and require strong, unique passwords across all systems to bolster security.
Technical measures are just as vital. Employ email filters to block phishing attempts before they reach inboxes and ensure all software is updated with the latest security patches. Encrypt data during transmission and while stored to safeguard it from unauthorised access. Regularly back up critical data to a secure, offline location and test your restoration process to ensure it works when needed. Additionally, having a well-defined incident-response plan will enable your team to act quickly and effectively if an attack occurs.
Tools like neoeco can further reduce risks. By automating data handling and removing manual processes, neoeco minimises potential entry points for phishing attacks. It also features built-in controls to detect unusual activity early, adding another layer of protection to your firm’s security strategy.
How does role-based access control improve data security for accounting firms?
Role-based access control (RBAC) strengthens data security by making sure employees can only access the information they need for their specific roles. By assigning permissions tailored to tasks like data entry, auditing, or management, organisations can significantly reduce the chances of unauthorised access or data breaches. This approach aligns with the principle of least privilege, which helps limit both accidental and deliberate exposure of sensitive client information.
RBAC also makes it easier to comply with UK regulations, such as GDPR. It allows firms to quickly update permissions when employees change roles or leave, ensuring the list of authorised users stays current. Additionally, it provides a clear audit trail, which is invaluable during inspections. Tools like neoeco’s accounting platform incorporate RBAC, giving firms control over who can view or edit financial and sustainability data. This not only safeguards confidential information but also streamlines compliance efforts and improves workflow efficiency for UK-based businesses.
What should an incident response plan include to handle data breaches effectively?
An incident response plan is a must-have for accounting firms to tackle data breaches swiftly, limit damage, and meet UK-GDPR obligations. Its core aim is to uphold confidentiality, integrity, and availability while ensuring that data access can be restored without unnecessary delays.
Here’s a streamlined approach to creating an effective plan:
Detect and report: Spot the breach, document all details, and alert the data protection officer within the required 72-hour window.
Contain the breach: Secure affected systems, disable compromised credentials, and block further unauthorised access.
Assess and classify: Determine the extent of the breach, identify the data involved, and evaluate its potential impact on stakeholders.
Notify relevant parties: Communicate with the ICO, affected clients, and any other necessary regulators, ensuring the information is clear and timely.
Eradicate and recover: Address the root cause, such as removing malware, bolster security measures, and restore data using verified backups.
Testing and updating your plan regularly is crucial to keeping it effective. Tools like neoeco, which integrate with financial ledgers and automate data handling, can also help reduce manual errors and enhance security processes.
Related Blog Posts

Deliver carbon accounting you can stand behind.
Built on real financial data, with full transparency and control — so every number holds up under scrutiny.
